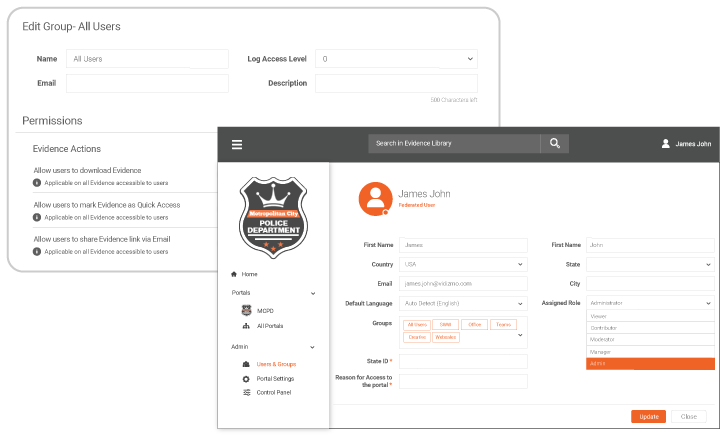
Authorized Access Management
VIDIZMO facilitates ease of access through centralized login credentials by integrating with several SSO identity providers such as Okta, Azure AD, PingID, SAMLP SSO, and many more.
Guard your Evidence with Various Security Controls
Ensure Evidence Integrity
Moreover, DEMS have the capability to detect evidence tampering through SHA cryptographic hash function, and can validate the credibility of your digital evidence.
Maintain Privacy for Different Stakeholders
Password Protect your Evidence

VIDIZMO is recognized as a Major Player in the 2020 IDC MarketScape
Key Security Capabilities

Role-Based Access Control
Assign a specific role to each user to control their access and permissions to perform various functions.

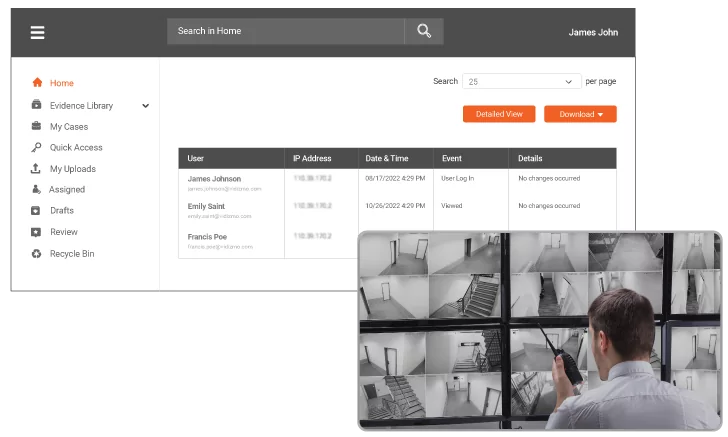
Audit Trails
Maintain a chronological list of records of all user activity and evidence handling to meet chain of custody requirements and monitor all activity across the system.

End-to-End Encryption
Ensure evidence security and protection with FIPS compliant AES-256 encryption at rest and in transit, and optional DRM support.

Access Reason Provisioning
Keep track of who and why someone accessed evidence by obligating users to provide valid reasons and details.

Password Protected Evidence
Control access to evidence by setting up password.
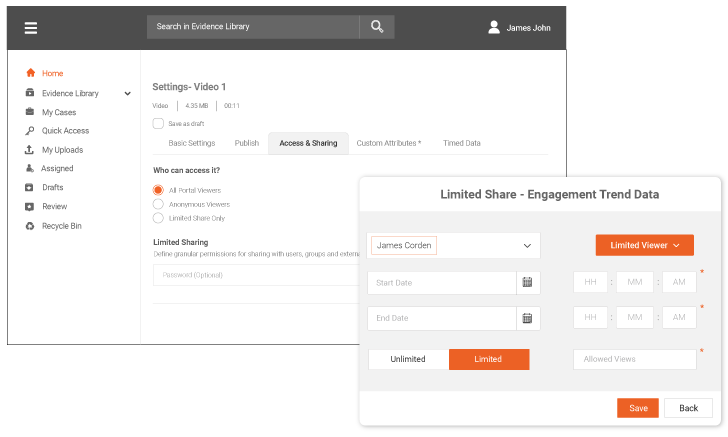
Limited Share
Restrict sharing through tokenized URLs, or search for specific groups/users, assign them editor or viewer roles, set limited views, and expiry date of the evidence.

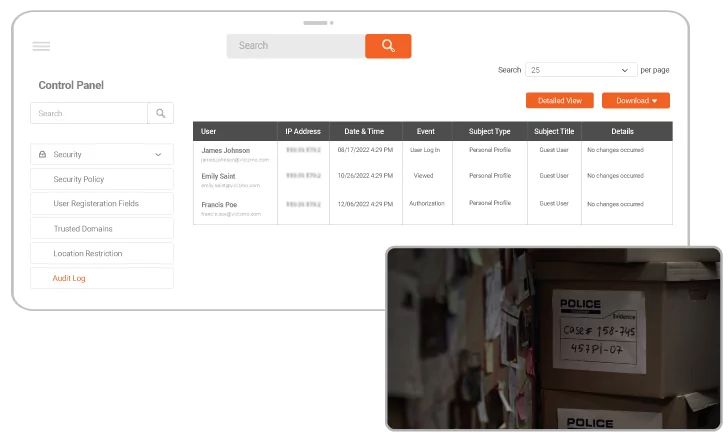
Security Policies
Use preconfigured security policies or create your own to control who can view or access a portal or the system.

Tamper Detection
Verify the integrity of your evidence files with the standard SHA cryptographic hash function to detect the presence of any tampering.

Evidence Alerts
Flag evidence to get alerts and notifications for certain events, such as evidence playback, tampering, downloading, modification, etc.

Users & Groups Management
Manage users and create groups to bulk manage access to evidence for multiple users.

Multiple Portals
Leverage different portals with autonomous security settings to segregate evidence and users.

Location and IP Restrictions
Restrict or enable specific or regional IP addresses from accessing the system.

Custom Purge Policy
Automate evidence purging by defining a retention policy.

Automatic Login Timeout
Set a time frame for inactivity after which a user is automatically logged out.

SSO Integration
Ensure authenticated and authorized access and add a layer to your digital evidence security with SSO integration.

